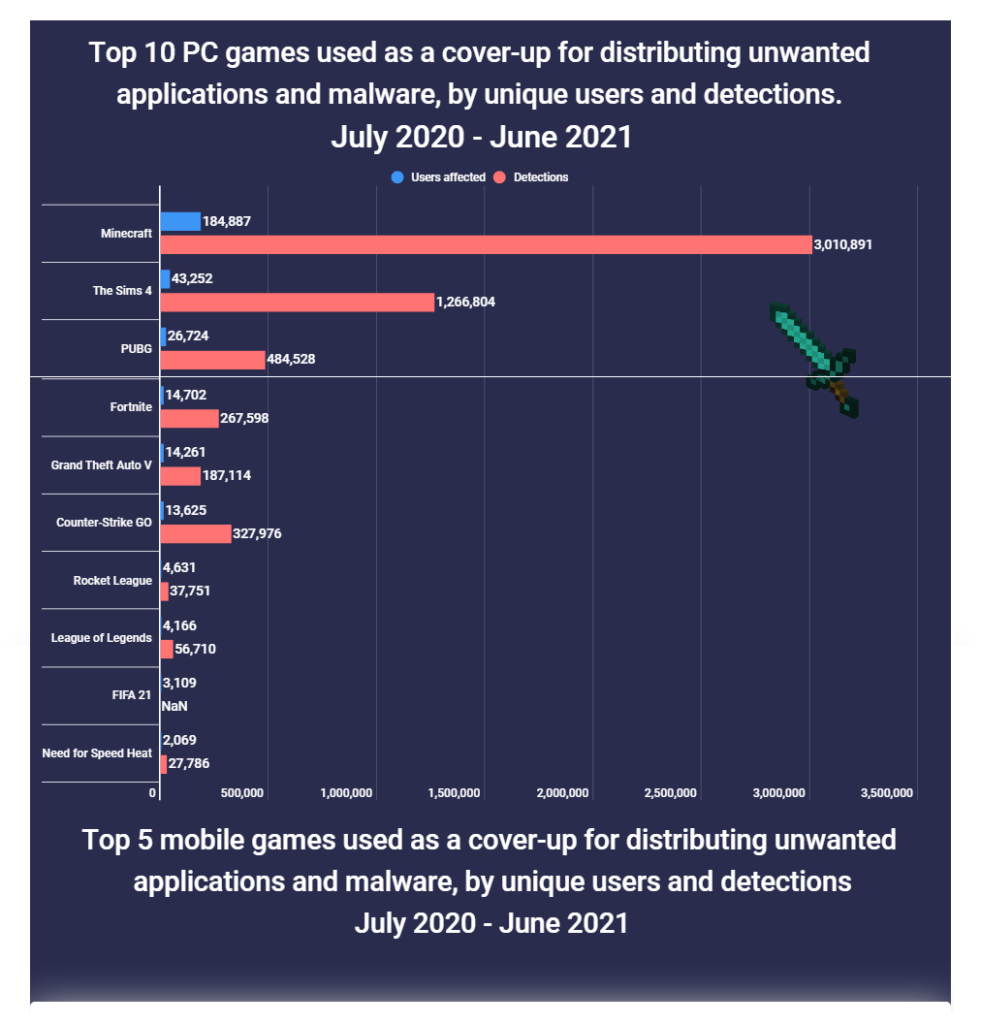
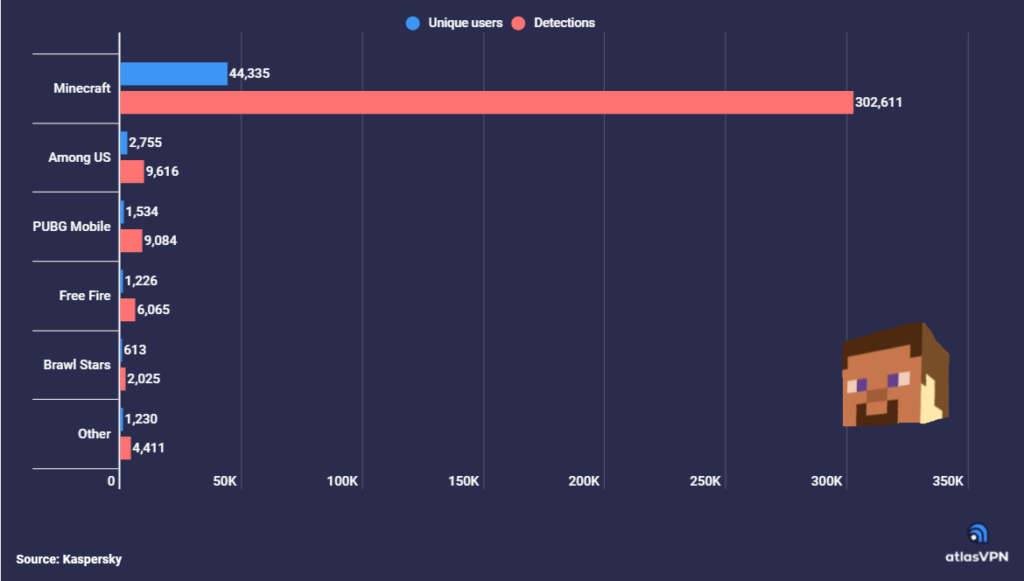
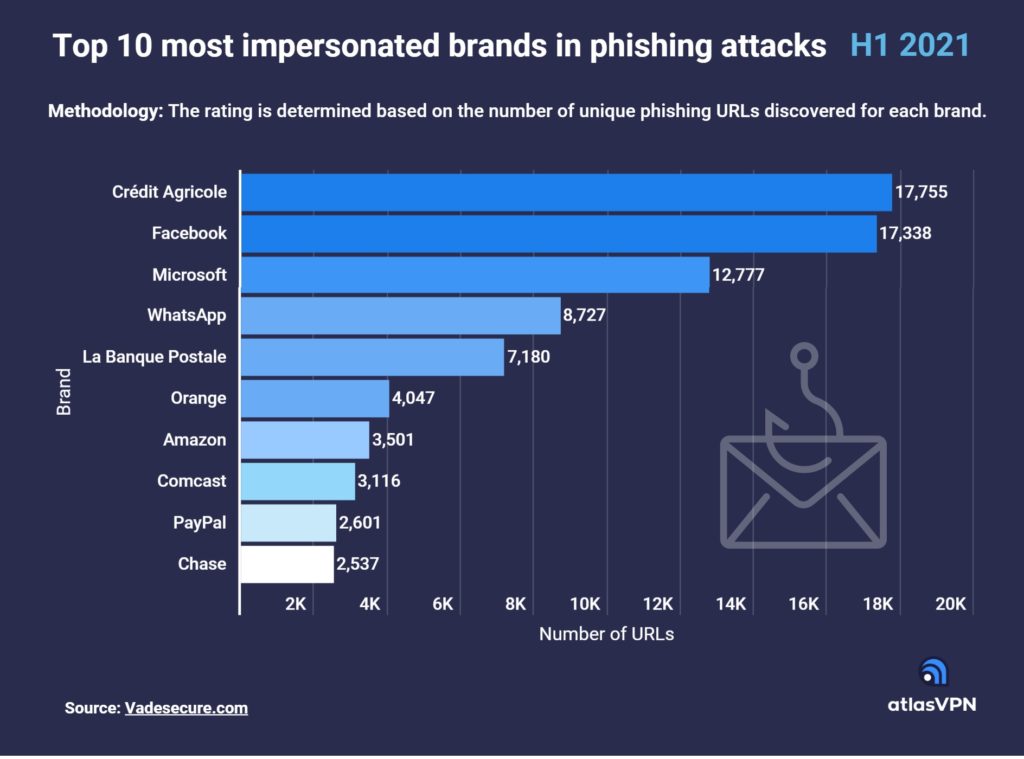
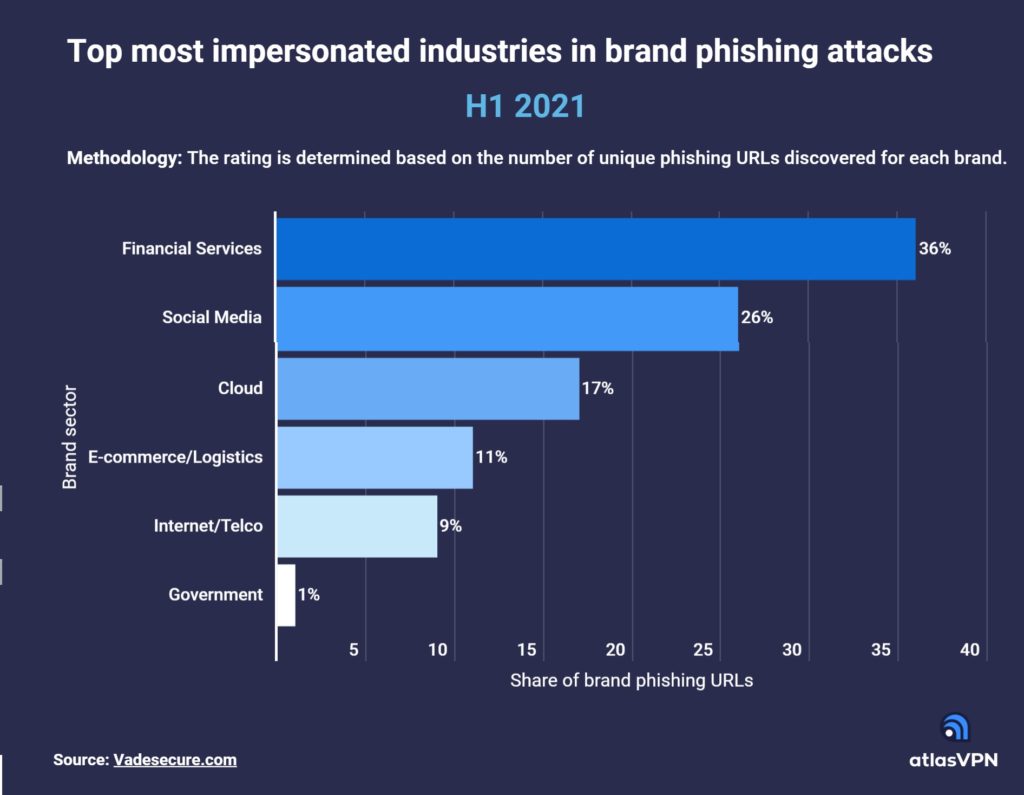
As the 2022 school year comes to an end, the surge of summer travel plans begins. With an estimated 60% of Canadians and Americans planning at least one trip over the next 3 months, hackers have roughly 200,000,000 projected tourists to prey on.
Lookout’s Cyber Security Expert, Hank Schless, shares how these cyber-attacks usually capitalize on travelers who are often overwhelmed or distracted when in unfamiliar environments, like airports and cafes.

>> Public Wifi Connections
“Although many airports offer free Wi-Fi connectivity, you should make sure that you join the official airport network and not a similar network that is configured to trick travelers into giving up their usernames and passwords”
- Attackers have been known to set up fake networks – with obvious but convincing names like ‘Starbucks_Guest_WiFi’.
- Once you connect, they’ll gain access to sensitive information, including your login credentials, emails, and messages.
- In order to protect yourself from wifi threats, alter your device’s settings so that it does not automatically connect to nearby networks, which the Lookout app does automatically.
>> Social Awareness & Juice Jacking
While on the go, travelers rely on power outlets and USB cords to keep their mobile device’s battery charged. Attackers can exploit USB chargers by loading malware onto them that infects your device the second you plug it in – Always be aware of your surroundings.

- If someone approaches you and offers their USB charging cord, it is best to decline.
- Always travel with your personal USB cords, and plug your charger directly into an electrical socket (vs USB port) if possible.
- The easiest place for a scammer to steal or hack your phone is in crowded areas – so never leave your phone or device unattended and only let people you know “borrow” your devices.
>> SMS and Email Travel Updates
“It’s important to be on guard for travel-related email, text, and social media scams as well. Attackers may try to steal a traveler’s credentials through phishing campaigns that pretend to be an airline, credit card company, or TSA”
- Here’s how it works: A scammer will send a message telling the recipient that their TSA PreCheck needs to be renewed, but the link in the renewal email leads to a fake site where hackers can accept payment and steal a victim’s personal information.
- Although the TSA sends renewal reminder texts and emails, travelers should always go directly to the TSA website for information on their existing accounts.
- For added protection, consumers can also download security – Security protection, like the Lookout app, will automatically monitor and identify scam URLs in email, text messages, and on the web and block you from threats that can do harm.