Criminals continue to impersonate well-known brands to trick people into giving up their personal information.
According to the data presented by the Atlas VPN team, Crédit Agricole, a French financial group, was by far the most used brand in phishing attacks in H1 2021. The brand was linked with 17,755 unique phishing URLs, followed by social media giant Facebook with 17,338 and Microsoft with 12,777.
The figures are based on Phisher’s Favorite Top 25 H1 2021 report by Vade, which looks at the 25 most impersonated brands in phishing attacks from January 1, 2021, to June 30, 2021.
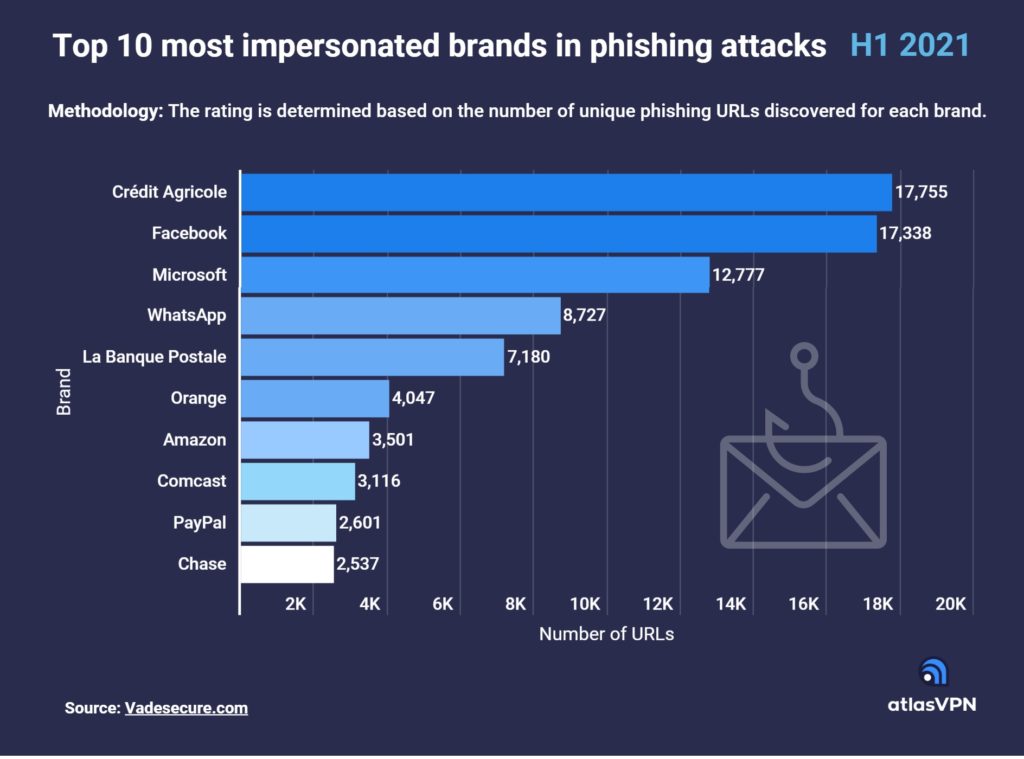
Multi-platform messaging service provider WhatsApp is the second social media brand to make the top ten list. It was taken advantage of in 8,727 phishing attacks. Meanwhile, French bank La Banque Postale occupies the fifth spot with 7,180 attacks.
Other brands in the top ten list include multinational telecoms company Orange (4,047), the world’s largest online retailer Amazon (3,501), multibillion-dollar media, entertainment, and communications company Comcast (3,116), digital payment service provider PayPal (2,601), and American national bank Chase (2,537).
Most phishing assaults were perpetrated in Brazil, followed by Russia and Indonesia.
Financial brands were criminals’ favorite
Generally, cybercriminals choose highly-trusted brands in their phishing campaigns. However, brands in certain industries were more favored than others.
Financial service brands were particularly popular in phishing attempts due to the rise in digital payments and growing reliance on online banking during the pandemic. They accounted for 36% of URL phishing attacks in H1 2021.
Cybercriminals spoofed well-known financial brands such as Crédit Agricole, La Banque Postale, PayPal, Chase, Wells Fargo, Square, HSBC, and Banque Populaire to lure out sensitive information from unsuspecting victims.
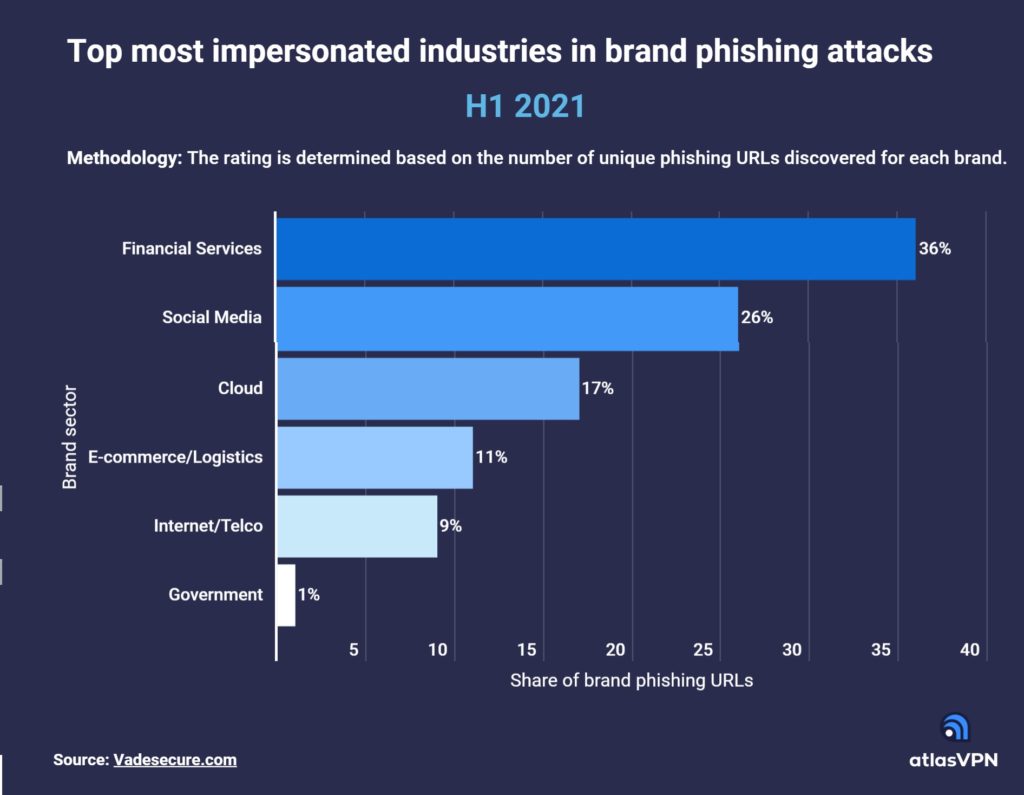
Social media companies were also heavily impacted. Social media brand impersonation accounted for over a quarter (26%) of all brand phishing attacks in the first half of this year. Apart from Facebook and WhatsApp, Instagram and LinkedIn were common choices for criminals.
Next up is the cloud sector. Cloud companies like Microsoft, Netflix, Adobe, and DocuSign were involved in 17% of URL phishing attacks. Meanwhile, 11% of phishing assaults targeted e-commerce and logistics companies, such as Amazon, DHL, Rakuten, Apple, and eBay.
The remaining 10% of brands spoofed in URL phishing attacks were internet and telecommunication companies, such as Orange, Comcast, Yahoo, SFR (9%), as well as government organizations (1%).
Tips to avoid phishing scams
- Keep your browser up to date. Look out for browser updates. They are released regularly and may contain security patches for vulnerabilities that were discovered on the browser. Cybercriminals often launch attacks to exploit known security vulnerabilities. Therefore it is essential to install any browser updates as soon as they become available.
- Inspect the website’s URL. Carefully inspect the website’s URL before taking any action. Criminals use visually similar characters such as lower case “L” and capital “I” to deceive people into thinking they are on a legitimate website.
- Look for an SSL certificate. Make sure the portal address starts with HTTPS (not with HTTP) and has a green padlock symbol before the web address. This means that the website has an SSL certificate, and the connection is encrypted.
- Beware of grammar mistakes. Scammers rarely hire professional writers to check their copy-cat website’s content for errors. If a website is riddled with spelling mistakes, there is a high chance it is not legitimate.
- Check if the website has been flagged. You can use URL checkers to see if the website has already been flagged. You can find many tools for this purpose by searching “Check URL safety” in Google.
- Use Tracker Blocker. Take advantage of the Atlas VPN Tracker Blocker tool, which stops third-party trackers and blocks malicious websites for a safer browsing experience.