How to avoid being hacked during this Fall’s travel season.
According to a recent study by cybersecurity firm NordVPN, one in four travelers has been hacked when using public Wi-Fi while traveling abroad. However, unsecured Wi-Fi is not the only factor travelers should be worried about.
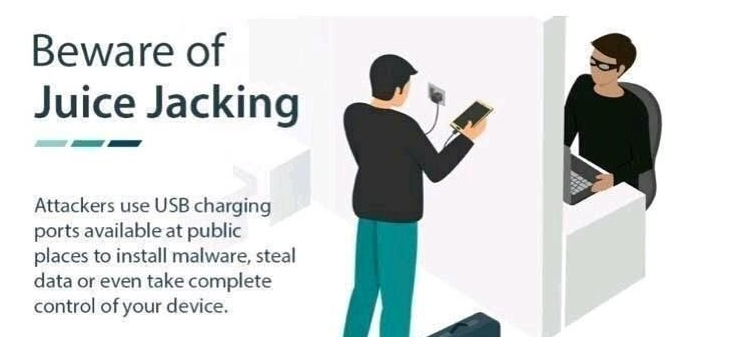
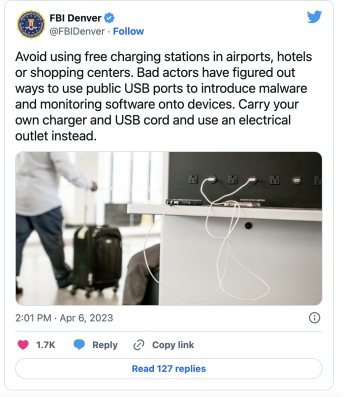
Last year, the FBI published a tweet (see below) warning users against smartphone charging stations in public places (airports, hotels, and shopping malls). Hackers may have modified the charging cables with the aim of installing malware on phones to perform an attack called juice jacking.
“Digital information, although it exists virtually, can also be stolen using physical devices. So it is important to take a 360-degree approach and secure your device from both online and offline threats,” says Adrianus Warmenhoven, a cybersecurity advisor.
What is juice jacking?
Juice jacking is a cyberattack where a public USB charging port is used to steal data or install malware on a device. Juice jacking attacks allow hackers to steal users’ passwords, credit card information, addresses, names, and other data. Attackers can also install malware to track keystrokes, show ads, or add devices to a botnet.
 |
Is juice jacking detectable?
Juice jacking attacks can be difficult to detect. If your device has already been compromised, you may notice some suspicious activity – but that won’t always be the case.
For example, you may notice something you don’t recognize on your phone — like purchases you didn’t make or calls that look suspicious.
Your phone may also start working unusually slowly or feel hotter than usual. Chances are you may have picked up malware. For a full list of signs to watch out for read on and find out how to know if your phone is hacked.
How to protect yourself
Since no sign of juice jacking is 100% reliable, it is best to avoid falling victim to this attack by using the following the advice:
- Get a power bank. Power banks are a safe and convenient way to charge your device on the go. Getting a portable power bank means that you’ll never have to use public charging stations where juice jacking attacks occur. Always ensure your power bank is fully charged so you can use it on the go.
- Use a USB data blocker. A USB data blocker is a device that protects your phone from juice jacking when you’re using a public charging station. It plugs into the charging port on your phone and acts as a shield between the public charging station’s cord and your device.
- Use a power socket instead. Juice jacking attacks only happen when you’re connected to a USB charger. If you absolutely need to charge your phone in public, avoid the risk of infected cables and USB ports and use a power outlet. This is typically a safe way to charge your mobile device and other devices in public.
For the Silo, Darija Grobova.